Wireless Networks on Campus
Note: If you're having issues getting your phone or device connected to the wireless network , we have instructions here:
Wireless Instructions
Services
Midwestern State University's Information Technology department is located on our Wichita Falls campus, in the McCullough Building. We provide the following services:
- Account creation, maintenance, and deletion
- Audio/Visual Equipment, Setup, Recordings
- Classroom Technology Quotes, Installation, Support
- Computer/Printing Lab Management
- Course Evaluations
- Data Backup, Storage, Reporting and Recovery
- Digital Signage
- Hard Drive Removal
- Hardware Quotes, Installation, Support
- Infrastructure
- Laptop Updates and Repairs (MSU property)
- Login Assistance
- Office technology Installation, Moves, Support
- Portal Login
- Software Vetting, Quotes, Installation, Support
- Telecommunications Services
- Third Party Application Support
- Wired and Wireless Infrastructure
Security Alerts
- Remote Access Scams
MSU IT wants to make you aware of remote access scams growing in intensity across the broader Internet.
Users affected by this type of scam may see a web browser screen pop up when browsing that warns of technical issues and urgently asks you to call a phone number or allow a technician to remotely access your computer. These notices will often say they are from Microsoft or Windows.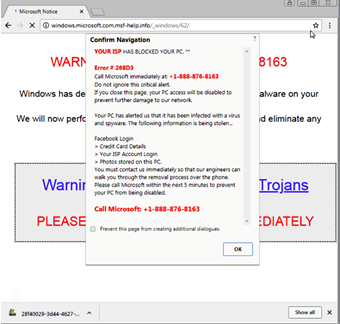
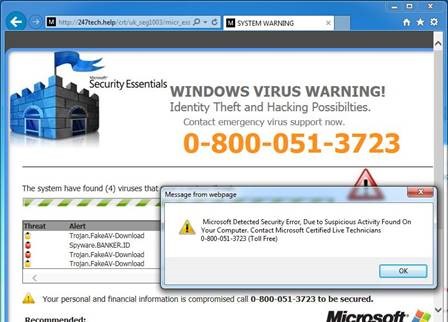
If you are ever asked to call a phone number or provide remote system access by ANY Internet resource you should immediately contact the Information Technology help desk at extension 4278 for guidance.
Users of Midwestern State University information resources should never provide remote access to any outside party without first consulting with MSU IT to validate the request.
** If you are presented with a screen similar to the examples shown above, turn off your computer immediately and call Information Technology at 4278. **
- Ransomware attacks
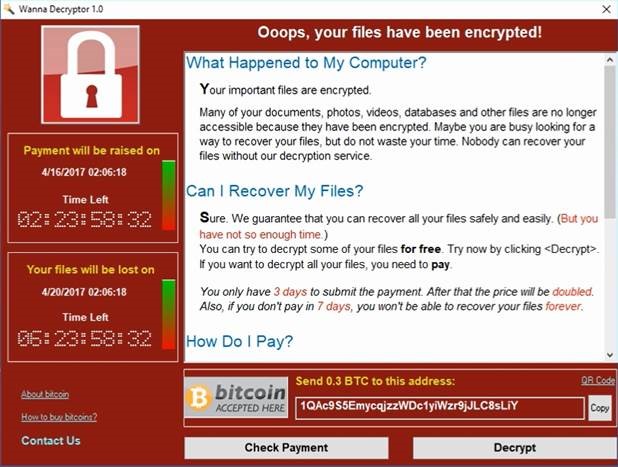
Ransomware is a type of malicious software, or malware, designed to deny access to a computer system or data until a ransom is paid. Ransomware typically spreads through phishing emails or by unknowingly visiting an infected website.
The ransomware presents a message like the examples shown below to infected users.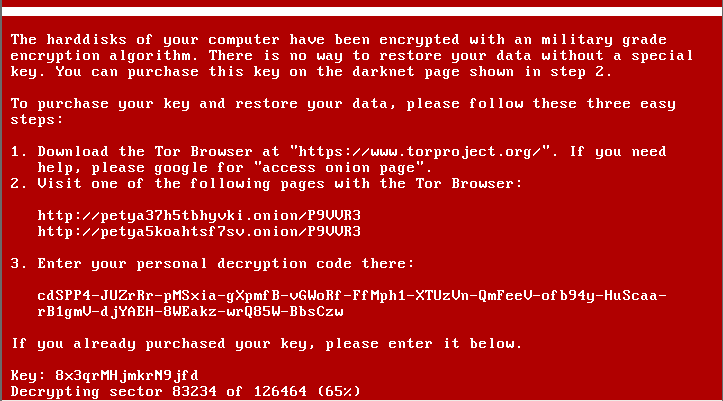
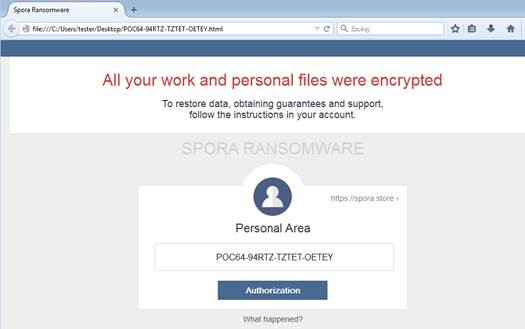
To help IT help you protect your digital resources please remember your training and watch for the following red flags when dealing with unexpected or unknown email:
- Were you expecting the email? If not take a much more critical view of opening the message and reach out to the purported sender to validate the message before clicking links or opening attachments.
- Inspect all aspects of the email. Mouse over the links without clicking them and if the link looks odd reach out to the purported sender to validate the message before clicking links or opening attachments.
** If you are presented with a screen similar to the examples shown above, turn off your computer immediately and call Information Technology at 4278. **
- Phishing Emails
Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers. Accounts from public email services such as Yahoo, Google, and Outlook.com that have been compromised can be used to send emails similar to the example shown below: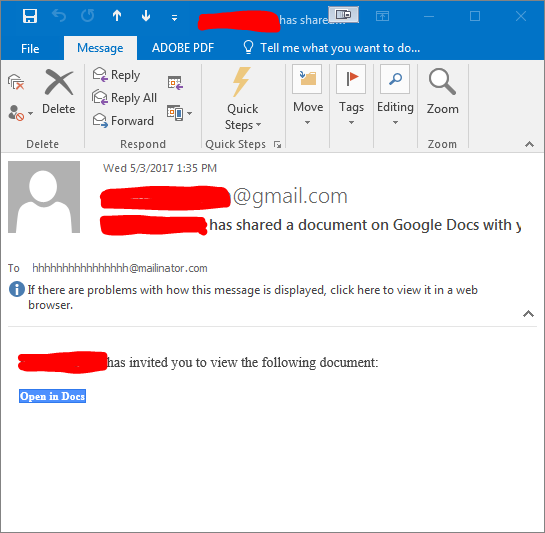
If you receive such an email, please forward it to phishingreports@msutexas.edu and then delete it immediately. Links like the “Open in Docs” link in the example above lead to malicious sites.
More information about security threats in your email (and elsewhere) can be found on MSU's Information Security pages.
Supported Hardware and Software
Supported Hardware and Software
To see a list of our minimum requirements for all hardware and software, including staff, faculty, and students, click here:
Supported Software and Hardware List
To see a list of our supported software for University-owned computers only, click here:
Staff and Faculty Supported Software
Students may access Microsoft Office 365 for free through the Microsoft website at the Office 365 for Students site.
If you are looking for a PC for personal use, we have partnered with Dell to offer discounts on select systems. Click below to see what they have available:
www.dell.com/msutexas