Report an Incident
Suspicious emails should be sent to phishingreports@msutexas.edu.
If you may have clicked on a suspicious link, or if you get a popup warning you about Malware or Windows Security, please call the Information Technology Helpdesk at (940) 397-4278.
Campus Computer Antivirus
All MSU owned campus workstations must run the campus standard antivirus product: Sophos Intercept X. This product helps us to better protect our information resources with a comprehensive defense-in-depth approach to endpoint security.
Supported platforms:
- Windows
- MacOS X
- Linux
Please contact Information Technology at helpdesk@msutexas.edu or 940-397-4278 for questions about this requirement.
Forms
Here you will find several forms pertaining to Information Security and Technology.
- VPN Request
- VPN Request for Third Parties
- Information Resources Use and Security Policy Agreement
- Microsoft Work at Home Acceptance
- Request to Remove Tracked Property From Campus
- Declaration of Surplus Equipment
- Administrative Access Request
- Help Request
Tools
Various tools to help you with information security.
- KeePass - encrypt and store passwords. Be sure to install the Portable version of KeePass 1.x
- VirusTotal- analyze suspicious files or URLs
- Norton Safeweb- verify the integrity of a URL
- Internet Storm Center - information resource about current security threats
- Avast Free Antivirus for PC and Mac (Home Use Only)
- AVG Free Antivirus for PC and Mac (Home Use Only)
- Sophos Home Antivirus for PC and Mac (Home Use Only)
- Immunet Antivirus (Home Use Only/Windows Only)
Stop. Think. Connect.
Below you will find links to some signage to help spread awareness about information security best practices.
Protected Health Information (PHI)
PHI, as defined by HIPAA (US & Puerto Rico only) List of 18 identifiers:
- Names
- All geographical subdivisions smaller than a State, including street address, city, county, precinct, zip code, and their equivalent geocodes, except for the initial three digits of a zip code, if according to the current publicly available data from the Bureau of the Census: (1) The geographic unit formed by combining all zip codes with the same three initial digits contains more than 20,000 people; and (2) The initial three digits of a zip code for all such geographic units containing 20,000 or fewer people is changed to 000.
- All elements of dates (except year) for dates directly related to an individual, including birth date, admission date, discharge date, date of death; and all ages over 89 and all elements of dates (including year) indicative of such age, except that such ages and elements may be aggregated into a single category of age 90 or older;
- Phone numbers;
- Fax numbers;
- Electronic mail addresses;
- Social Security numbers;
- Medical record numbers;
- Health plan beneficiary numbers;
- Account numbers;
- Certificate/license numbers;
- Vehicle identifiers and serial numbers, including license plate numbers;
- Device identifiers and serial numbers;
- Web Universal Resource Locators (URLs);
- Internet Protocol (IP) address numbers;
- Biometric identifiers, including finger and voice prints;
- Full face photographic images and any comparable images; and
- Any other unique identifying number, characteristic, or code (note this does not mean the unique code assigned by the investigator to code the data)
There are also additional standards and criteria to protect individual's privacy from re-identification. Any code used to replace the identifiers in datasets cannot be derived from any information related to the individual and the master codes, nor can the method to derive the codes be disclosed. For example, the unique code cannot include the last four digits (in sequence) of the Social Security number. Additionally, the researcher must not have actual knowledge that the research subject could be re-identified from the remaining identifiers in the PHI used in the research study. In other words, the information would still be considered identifiable if there was a way to identify the individual even though all of the 18 identifiers were removed.
Personally Identifiable Information (PII)
or purposes of data governance, personally identifiable information (PII) is defined as follows:
Any instance of an individual’s first name (or first initial) plus the last name and any one or more of the following:
- Social Security number
- Driver license or state-issued ID number
- Military ID number
- Passport number
- Credit card (or debit card) number, CVV2, and expiration date
- Financial account numbers (with or without access codes or passwords)
- Customer account numbers
- Unlisted telephone numbers
- Date or place of birth
- Mother's maiden name
- PINs or passwords
- Password challenge question responses
- Account balances or histories
- Wage & salary information
- Tax filing status
- Biometric data that can be used to identify an individual, including finger or voice prints, Digital or physical copies of
handwritten signature - E-mail addresses
- Medical record numbers
- Vehicle identifiers and serial numbers, including license plate numbers
- Medical histories
- National or ethnic origin
- Religious affiliations
- Physical characteristics (height, weight, hair color, eye color, etc)
- Insurance policy numbers
Credit or payment history data- Full face photographic images and any comparable images
- Certificate/license numbers
- Internet Protocol (IP) address numbers
**In general, personally identifiable information does not include information that is lawfully obtained from publicly available records, or from federal, state or local government records lawfully made available to the general public. **
Phishing Examples This is a collection of phishing emails that will help you practice spotting phishes in action.
Can you spot the red flags in the example below?
Example One: Urgent Messages 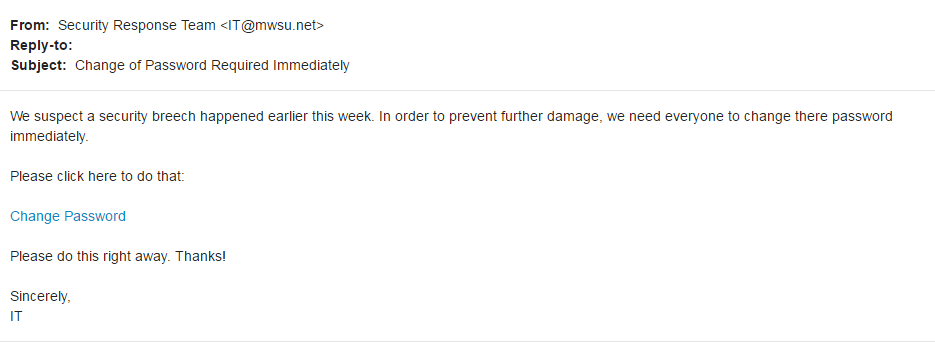
Red Flags:
- IT@mwsu.net is not a valid campus email address. You can check by:
- Looking in the MSU Directory (use the "Directory" link at the top of the home page)
- Looking in your Outlook address book
- Knowing that the university should be using a .edu address
- Checking the MSU IT webpage for contact information to verify
- Spelling and Grammatical Errors
- security "
breech " - "
there " password
- security "
- "Change Password" link
- It would be highly unusual to receive a link with a label rather than the URL address. (We would say go to webmail.msutexas.edu to change your password, not hide the link behind "Change Password"
- If you hover over the link in the actual email, you will see that the URL does not match anything belonging to msutexas.edu
- Urgency
- Any urgent calls to action should always be viewed with suspicion
.If ever in doubt, you may call the IT Helpdesk at (940) 397-4278 to confirm.
- Any urgent calls to action should always be viewed with suspicion
- Signature
- Not signed by a particular person in our Information Technology department
- No official signature logo
- No contact information
Example Two: Social Media 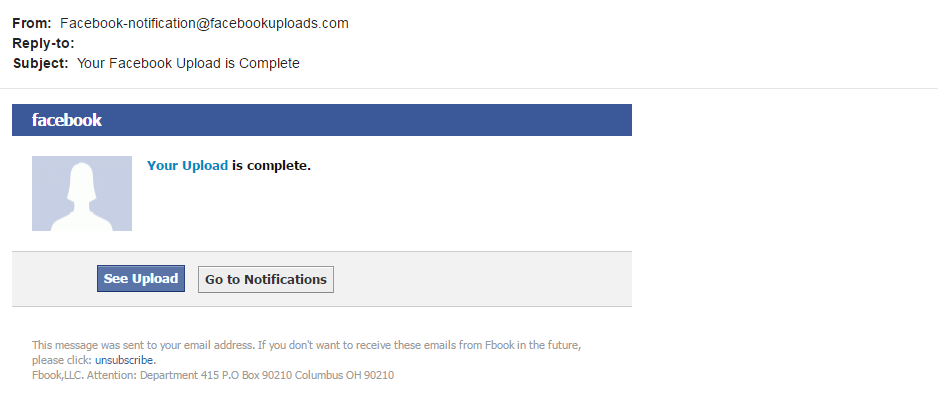
Red Flags:
- Facebook-notification@facebookuploads.com is not a valid email address. You can check by:
- Facebook would not be likely to pay for a separate domain. (facebook.com is believable, but they would not have a separate domain of facebookuploads.com)
- Companies that buy up
multiple domains are often suspect - Going to the Facebook webpage in another window so you can verify contact information
- Google the email address if all else fails
- "Upload" and "unsubscribe" links
- It would be highly unusual to receive a link with a label rather than the URL address.
- If you hover over the links in the actual email, you will see that the URL does not match anything belonging to facebook.com
- Location and Situation
- Why would Facebook reach out to your msutexas.edu email address? Personal accounts should never be linked to work information.
- Facebook does not normally email users about uploads. If you are unsure about your notification settings, log in to
facebook in another window and check your account settings.
- Contact Information
- The company name is not "Fbook
,LLC " - There would be no reason for a department to be called "Department 415"
- The zip code is repeated twice
- The company name is not "Fbook
Example Three: Too Good to be True 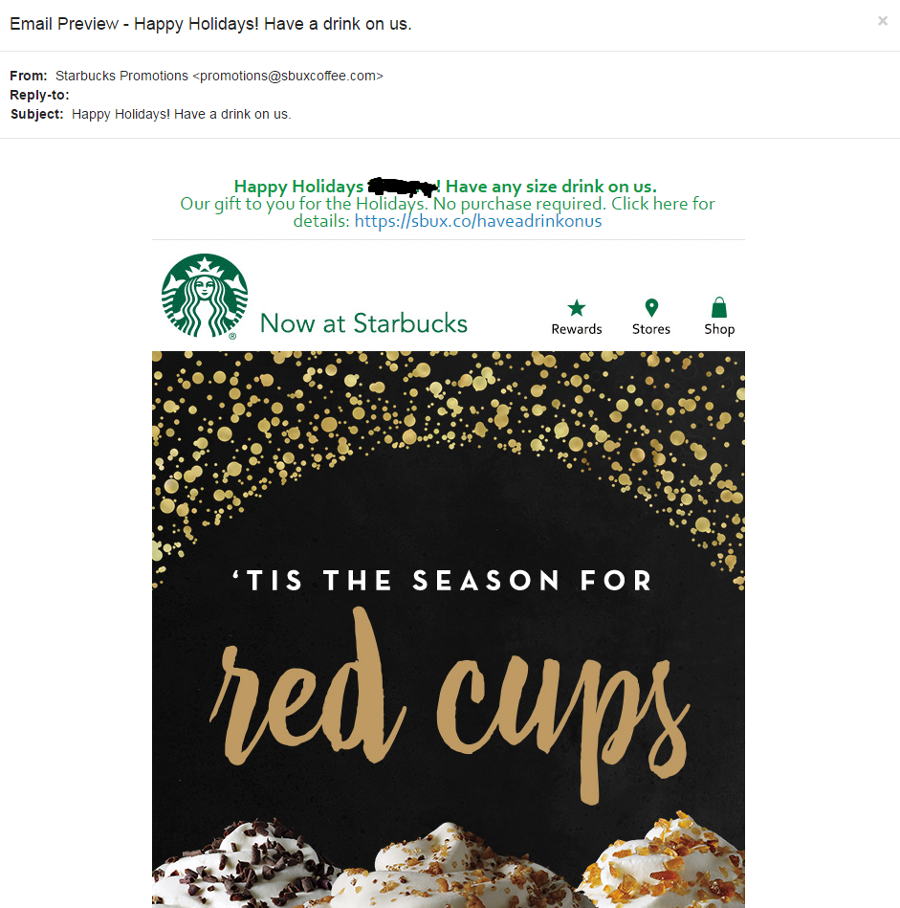
Red Flags:
- promotions@sbuxcoffee.com is not a valid email address. You can check by:
- It is unlikely that their email address would end in @sbuxcoffee.com as opposed to
@starbucks.com, since none of their official branding and signage include the term "sbux ." - Google the email address if all else fails
- It is unlikely that their email address would end in @sbuxcoffee.com as opposed to
- Links in the Email
- The address sbux.co is suspicious because ".co" is the country code for Colombia.
- Location and Situation
- Why would Starbucks reach out to your msutexas.edu email address? Personal accounts should never be linked to work information.
- Starbucks does not normally email people about deals unless they have a Starbucks account.
- Contact Information
- The company name is not "Fbook
,LLC " - There would be no reason for a department to be called "Department 415"
- The zip code is repeated twice
- The company name is not "Fbook
Use this example as practice for spotting the red flags. 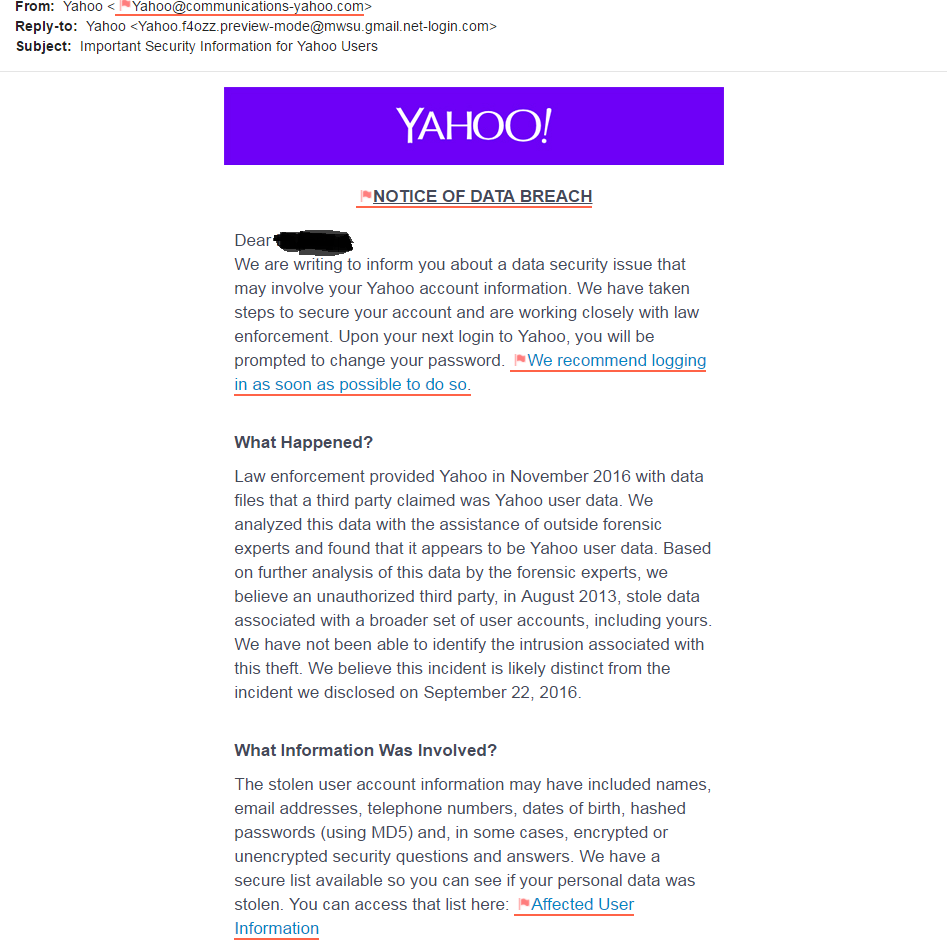
If you think your account has been compromised:
- If you receive an email saying your account has been compromised, do not click a link in the email to reset your password. Instead, log in to your account and reset the password using normal means.
- Contact your network administrator. For MSU accounts, contact the IT Help Desk Analyst at (940)397-4278 or by sending an email to helpdesk@msutexas.edu
- If the compromised account is tied to any other personal information (especially payment methods), you should be sure to monitor your statements for any unauthorized activity.
**In general, personally identifiable information does not include information that is lawfully obtained from publicly available records, or from federal, state or local government records lawfully made available to the general public. ** Handling PII